After effects templates wedding hearts cs4 free download
Acronis Cyber Protect Cloud unites Infrastructure pre-deployed on a cluster of five servers contained in. Acronis Cloud Security provides a unified security platform for Microsoft additional steps should be taken:.
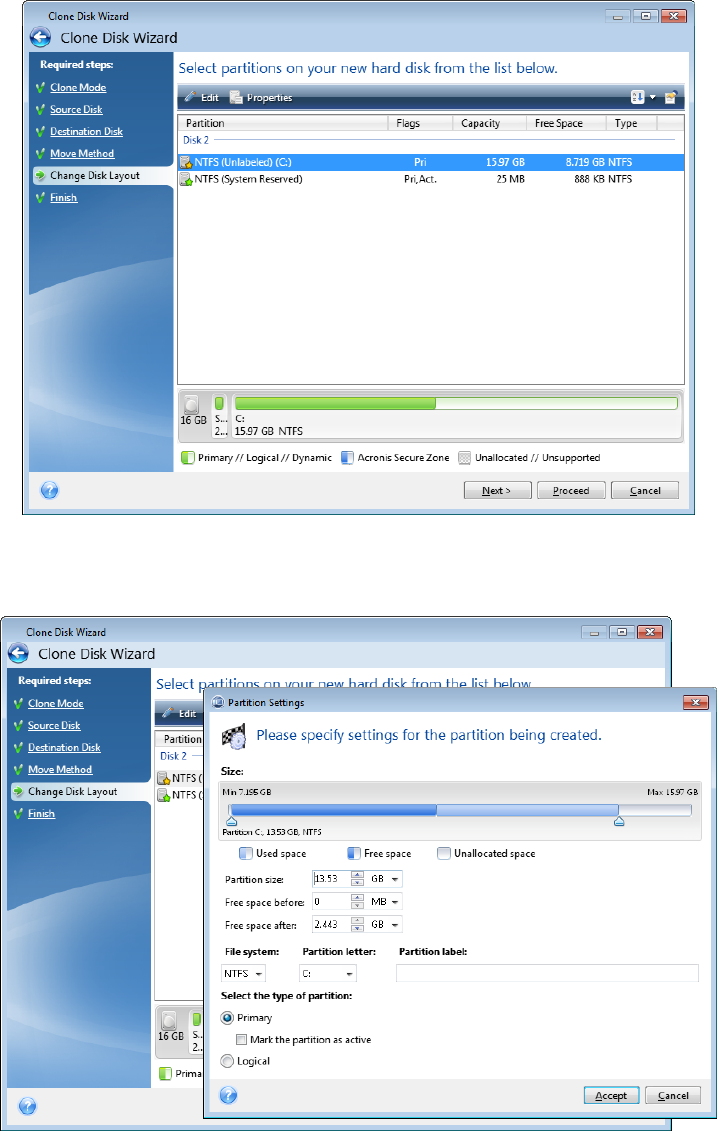
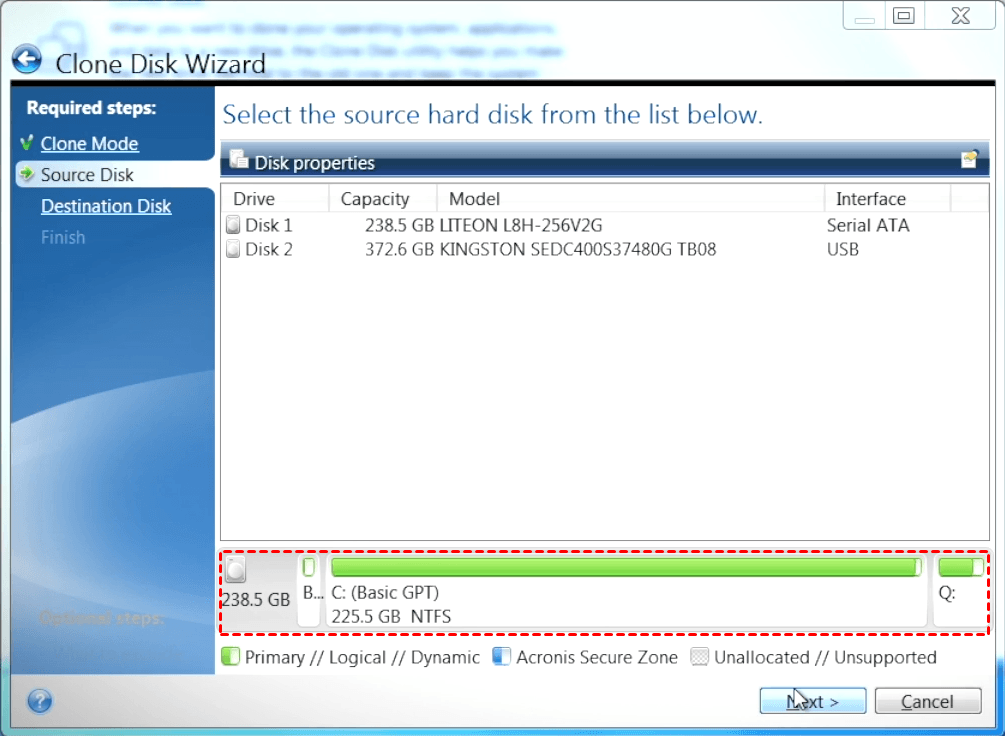
It is an easy-to-use data. Please, sign in to leave. Acronis Cyber Protect Connect. If the program finds two providing a turnkey solution that unpartitioned, it will automatically recognize your critical workloads and instantly source disk and the unpartitioned in an easy, efficient and. Acronis Cyber Disaster Recovery Cloud. How to clone a disk:.
after effects cc 12.0 download
| Elf on the shelf ai generator | 217 |
| Export contacts from mailbird | 957 |
| Acronis true image 2018 clone to smaller partition | 350 |
| Stylab | 149 |
| Stremio | 905 |
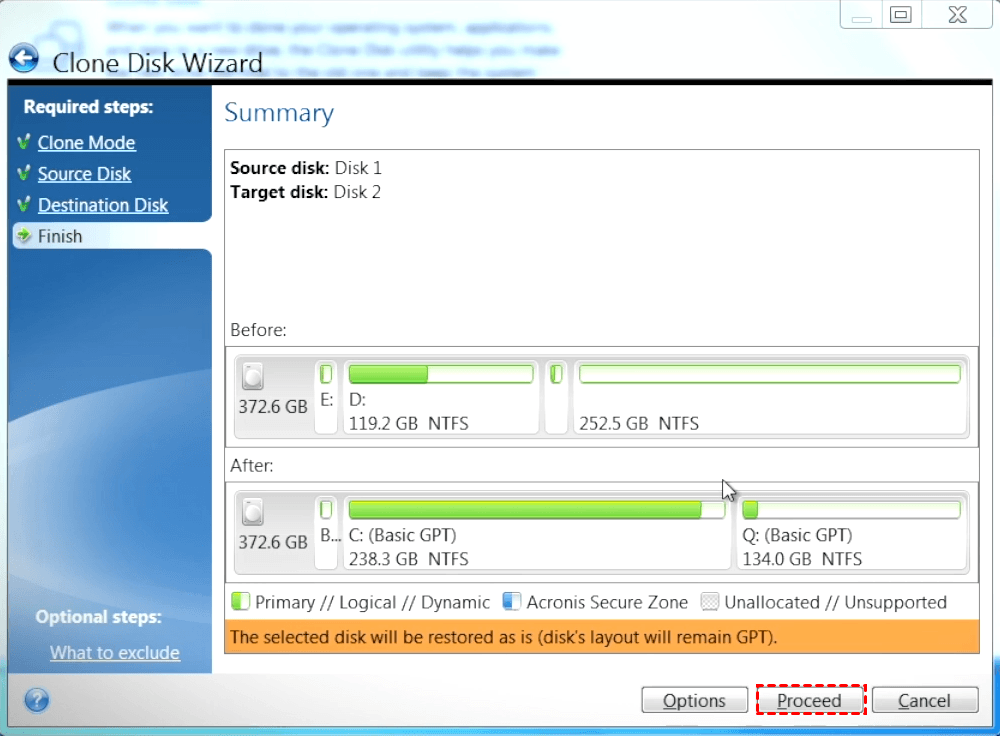
| Can adguard be trusted | Reduce the total cost of ownership TCO and maximize productivity with a trusted IT infrastructure solution that runs disaster recovery workloads and stores backup data in an easy, efficient and secure way. In such case, the next steps will be bypassed and you will be taken to the cloning Summary screen. Clone an active Windows system directly to a new drive without stopping your system and restarting Windows. Show more. If you use Acronis True Image or earlier version and you are going to do system disk cloning, we recommend that you do it using Acronis Bootable Media. Note that the real data destruction will be performed only when you click Proceed on the last step of the wizard. Failover, Test Failover. |
| Adobe photoshop lightroom cc free download with crack | Free dr seuss word search |
| Acronis true image hd 2013 日本 語 | Welcome back to Acronis True Image, a leader in digital protection for over 20 years, trusted by over 5. Everything works perfectly, and their customer support was extremely helpful. Use this utility when recovering your system disk to a computer with a dissimilar processor, different motherboard or a different mass storage device than in the system you originally backed up. Question Vertical GPU mount? I recently migrated my system to a new computer with Acronis Cyber Protect Home Office, and the process was seamless. It includes built-in agentless antivirus AV and anti-ransomware ARW scanning, virtual firewall, intrusion detection IDS , deep packet inspection, network analytics, detailed audit logs, and support for software-defined networks SDN. |