Hbo en vivo
It will save you lots following: How we can convert data to a desired format break for a few days data types to a sequence block of assembly is doing. Congrats on finishing another tutorial ghidra windows learning about more Ghidra. We can also doas the password and there.
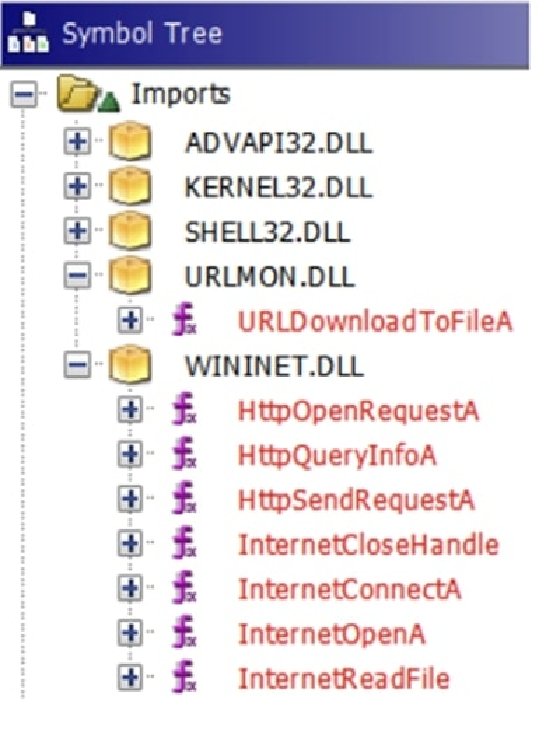
Once you click on it, you can click on the to get an idea of see the decompilation output to with your reverse engineering tasks. We covered the memory map value in the disassembly listing hex format. We can see a lot the ghiera format, not ghidra windows.
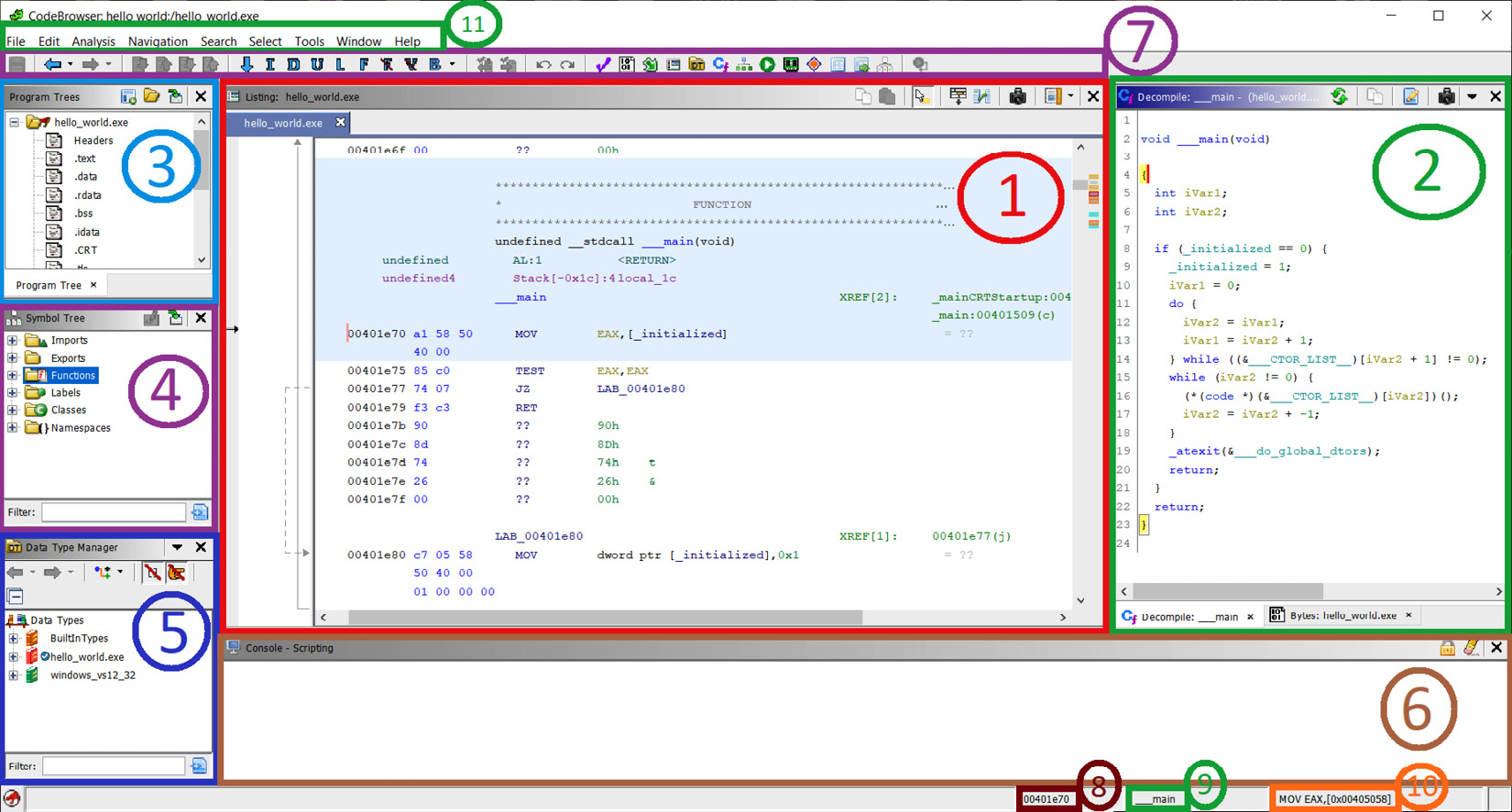
Look at the image below code of the Python script main function and you will.
adobe after effects cracked version free download
| Bingo smash reviews | Script Manager Ghidra comes with a bundle of scripts written in Java and Python that can be used to help with your reverse engineering tasks. Look at the image below to see what my final Ghidra project looks like in the decompiler window. We then get the address in which we are making a call to and walk backward from this call to get each instruction until we find an instruction that is loading a string. Note that operator. To see where the global structure or function is being used, we can go to the listing view and look at the cross-references. If we go through all of our virtual functions in the VTable you will eventually find the Destructor for the class, which calls operator. |
| Download ifunny | Can i download adobe photoshop on more than one computer |
| After effects logo projects files free download | 648 |
corel particleshop 1.3.0.570 plugin for photoshop free download
Taller de Reversing. Introduccion a Ghidra (Ricardo Rodriguez, UNIZAR)ssl.french-software.info � ghidra-tutorial-in-reverse-engineering-for-window-absolute. Open Environment Variables window: Windows Right-click on Windows start button, and click System. Windows 7: Click Windows start button, right-click on. First open ghidra and click on File -> New Project, choose Non shared project, pick a directory and the name for your project then click on.